
News overview
Q3 2021 brought two new DDoS attack vectors, potentially posing a serious threat, including for major web resources. A team of researchers from the University of Maryland and the University of Colorado Boulder found a way to spoof the victim’s IP address over TCP. To date, amplification attacks have mostly been carried out using the UDP protocol, since it does not require connection establishment procedures and allows IP spoofing. In contrast, the TCP protocol implements a three-way handshake in which the client and the server establish a connection and confirm they are ready to exchange traffic. If the victim receives a response from the server to a request they did not send, they simply discard this response.
The new attack, as described by the researchers, targets security devices located between the client and the server (so-called middleboxes) — firewalls, load balancers, network address translators (NAT), deep packet inspection (DPI) tools and others. Many of them can interfere with a TCP connection, for example, by blocking a connection to a banned resource, and they often react to packets received from one of the parties without seeing the full picture or monitoring the validity of the TCP session. If a request for access to a banned resource is sent under the guise of the victim, the response from a middlebox can be significantly larger. As such, the researchers found more than 386,000 devices giving an amplification factor of over 100, with more than 97,000 of them over 500, and 192 of them over 51,000.
The second attack, described by Nexusguard and dubbed Black Storm, can target any network device. An attacker can send requests to closed ports on devices in a communications service provider (CSP) network under the guise of other devices in the same network. Receiver devices respond to such requests with a message stating that the port is unavailable. Processing these messages consumes a lot of resources, which overloads victim devices and prevents them from accepting legitimate requests. The researchers note that this method allows an attacker to take down not only individual servers, but the provider’s entire network, including a large one.
Another high-profile event of the quarter was the discovery of Mēris, a new botnet capable of carrying out powerful DDoS attacks. According to Yandex and Qrator Labs, who were the first to report the botnet, it is made up of high-performance network devices, mainly from Mikrotik, and uses HTTP pipelining, which allows multiple requests to be sent to a server within a single connection without waiting for a response. Attacks by this botnet are notable for the huge number of requests per second. For instance, a DDoS attack on a Cloudflare customer (attributed to Mēris) clocked in at 17.2 million requests per second, despite lasting less than a minute, while Yandex reported 21.8 million requests per second.
The website of Brian Krebs, a well-known journalist in the field of information security, was also subjected to a brief, but powerful, Mēris attack. Krebs notes that, while the requests-per-second rate was not as impressive as in the case of Yandex or Cloudflare, it was still more than four times as powerful as the Mirai attacks on his site.
Another information security media, Infosecurity magazine, hit by a DDoS attack, decided to switch to a more robust hosting provider. While the site was unavailable, staff got creative: they began uploading podcasts to SoundCloud, which they informed readers about on Twitter.
We won't let our #DDoS stop us doing what we love! So, here's our BRAND NEW IntoSecurity Daily #podcast -a round up of all the TOP news headlines you need to know each day in a snappy bite-size format with our editorial team @InfosecEditor @ReporterCoker https://t.co/gR7D54BSYT pic.twitter.com/AAYehW8Ux0
— Infosecurity Magazine (@InfosecurityMag) July 26, 2021
In Q3, a wave of large-scale DDoS attacks swept across New Zealand, at least some of which, according to Yandex and Qrator Labs, were the work of that same Mēris botnet. Specifically, the researchers attribute the attack on a customer of Vocus, a major New Zealand provider, to the shenanigans of the new zombie network, which led to a short-term disruption of service nationwide. To stop the attack, the company updated a rule on its DDoS mitigation platform, and it was this rule change that reportedly caused the outage. Besides the unnamed Vocus customer, the DDoS surge in New Zealand also overwhelmed the banks ANZ and Kiwibank, the mail service NZ Post and the weather service MetService.
A notable trend of the third quarter appeared in the form of ransom attacks on VoIP providers, which affected companies in Britain, Canada and the US. Powerful and complex, they caused both voice and messaging issues for customers. The cybercriminals, who claimed to be from the ransomware group REvil, demanded a huge ransom to stop the attack. However, it is not possible to confirm the group’s identity as REvil or someone else. At any rate, the ransom attacks on VoIP providers were limited to DDoS, while REvil primarily does data encryption, although the group does not shrink from other methods of putting pressure on companies.
Also hit by a ransom DDoS attack was one of the oldest Bitcoin sites, Bitcoin.org. Though in this case, unlike the attacks on VoIP providers, the cybercriminals were willing to settle for half a bitcoin, for a non-profit information portal this is still a hefty amount.
Malware operators in Q3 also decided to use DDoS as an intimidation tool. The attackers sent out e-mails to companies saying their resources were being used in DDoS attacks and they could face legal problems. The messages contained a link to a cloud directory supposedly with details about the incident, which actually contained the BazarLoader malware loader.
In some countries, DDoS attacks have targeted sites set up to help fight COVID-19. In August, attackers tried to take down a vaccination registration portal in Manila. And in September, they went after the Dutch website CoronaCheck, where people can get QR codes required to visit cafes and cultural sites. As a result, users could not generate QR codes, and their attempts to get a response only made the situation worse.
Q3 saw a number of politically motivated DDoS attacks in various countries. For example, in early and mid-July, unknown actors flooded the resources of the security agencies of Russia and Ukraine with junk traffic. And in the last third of the month, the Russian newspaper Vedomosti became a DDoS victim. Most likely, the attack was linked to one of its online articles. In mid-August, attackers tried to stop users from accessing the web resources of the Philippine human rights organization Karapatan. Then, at the end of the month, the website of Germany’s Federal Returning Officer was briefly targeted in connection with the September 26 elections to the Bundestag.
As per tradition, gaming platforms didn’t escape cybercriminal attention either. In Q3 2021, the European servers of Final Fantasy XIV were hit. For several hours, gamers experienced dropouts, slowdowns and login issues.
On the other side of the coin, Ubisoft, the developer of Tom Clancy’s Rainbow Six Siege, having also been plagued by junk traffic, won a lawsuit this quarter against a cybercriminal group that had distributed software for DDoS attacks on the game. The accused were ordered to pay the company US$153,000 in damages, as well as to cease operations and hand over any relevant domains.
Another actor, the operator of two “stressers” (used to carry out DDoS attacks) was found guilty of cybercrime in court. Sentencing will not take place until January 2022. It could be harsh: up to 35 years in prison. According to the investigators, one of the stressers alone was used to attack more than 200,000 targets, including government, financial, educational and gaming sites.
The fate of the WireX botnet operator, who attacked an international hotel chain in 2017, is a little more hazy. The US Department of Justice filed charges in September 2021, but the perpetrator has yet to be caught. Law enforcers believe the individual is currently in Turkey.
Quarter trends
Q3 was certainly interesting and certainly not calm: contrary to our expectations, we observed growth uncharacteristic for this period.

Comparative number of DDoS attacks, Q2 and Q3 2021, and Q3 2020. Q3 2020 data is taken as 100% (download)
On the topic of DDoS attacks in Q3, we should mention an unusual attack, data for which was not included in the above statistics. It occurred in August, and the target was the online accounts of applicants at a state university. The attack was hybrid, carried out at the L4 and L7 levels, and several days in duration, even lasting more than 48 hours after the target resource was placed under the watchful eye of Kaspersky DDoS Protection. The attack is interesting for two reasons. First, the attackers chose vectors that rendered the resource completely unavailable. Second, it is rather unusual that the attack continued long after filtering began. Continuing an attack when it no longer impacts the availability of the target resource makes no sense: it only increases the detection risk for botnet hosts. Accordingly, in the vast majority of cases, attacks cease as soon as effective traffic filtering begins. These two nuances suggest, at the minimum, that the attack organizers have above average technical knowhow and financial backing. The motives behind the attack are unclear, and although DDoS offensives on the education sector in Q3 are never a rarity, this one looks too sophisticated and high-end for simple teenage pranking.
Statistics
Methodology
Kaspersky has a long history of combating cyberthreats, including DDoS attacks of any type and complexity. Company experts monitor botnets using the Kaspersky DDoS Intelligence system.
A part of Kaspersky DDoS Protection, the DDoS Intelligence system intercepts and analyzes commands received by bots from C&C servers. The system is proactive, not reactive, meaning that it does not wait for a user device to get infected or a command to be executed.
This report contains DDoS Intelligence statistics for Q3 2021.
In the context of this report, the incident is counted as a single DDoS-attack only if the interval between botnet activity periods does not exceed 24 hours. For example, if the same resource is attacked by the same botnet after an interval of 24 hours or more, two attacks will be counted. Bot requests originating from different botnets but directed at one resource also count as separate attacks.
The geographical locations of DDoS-attack victims and C&C servers used to send commands are determined by their respective IP addresses. The number of unique targets of DDoS attacks in this report is counted by the number of unique IP addresses in the quarterly statistics.
DDoS Intelligence statistics are limited to botnets detected and analyzed by Kaspersky. Note that botnets are just one of the tools used for DDoS attacks, and that this section does not cover every single DDoS attack that occurred during the review period.
Quarter summary
- In Q3, 40.80% of DDoS attacks were directed at US-based resources. The resources themselves accounted for 42.13% of all unique targets.
- Hong Kong made it back to TOP 3 both by the number of DDoS attacks (15.07%) and the unique targets count (14.36%).
- Q3 has beaten every record in terms of daily number of DDoS attacks: on August 18, we observed 8,825 attacks, with over five thousand on August 21 and 22.
- The average and maximum durations of DDoS attacks in Q3 decreased to 2,84 and 339 hours respectively.
- In Q3, most DDoS attacks took the form of SYN flooding.
- Most of the botnet C&C servers were in the US (43.44%), while the bulk of the bots attacking Kaspersky honeypots operated from China.
DDoS attacks geography
In Q3 2021, the share of attacks on US-based resources increased by 4.8 p.p. to 40.80%. The country keeps its first place by the number of DDoS attacks. The Hong Kong Special Administrative Region has stepped up to the second position (15.07%). Following a calm period in Q1 and Q2, the region’s share of attacks grew all at once by as many as 12.61 p.p. Whereas, China’s share (7,74%) shrank yet again, landing the country in third.
The fourth place is still held by Brazil (4.49%), its share but slightly reduced. South Africa rose to fifth (3.09%) adding 3 p. p. and pushing Canada (3.07%) to sixth. Canada is followed by Germany (2.88%), France (2.78%) and the UK (2.72%), with Singapore at the foot of the ranking (2.35%).

Distribution of DDoS attacks by country/region, Q2 and Q3 2021 (download)

Distribution of unique targets by country/region, Q2 and Q3 2021 (download)
Dynamics of the number of DDoS attacks
Q3 was unusually explosive for the number of DDoS attacks. July started off relatively quietly, but towards the middle of the month the average daily count of DDoS attacks exceeded 1,000, with a whopping 8,825 attacks on August 18. For two more days, August 21 and 22, the daily count of five thousand was exceeded, and over three thousand attacks were detected on August 2 and 6, September 16, 18, 19 and 22.

Dynamics of the number of DDoS attacks, Q3 2021 (download)
In Q3, the distribution of DDoS attacks by day of week was the least homogenous of the year: the difference between the most active and most quiet day reached 7.74 p.p. Most of the attacks occurred on Wednesdays — 19.22%. In no small part the statistics was influenced by the DDoS upsurge of Wednesday, August 18. The share of attacks that took place on Saturdays and Sundays also grew due to the other two August peaks. On other days of week the share of DDoS activities reduced from the previous quarter. Most of the time, cybercriminals were off on Mondays (11.48%).
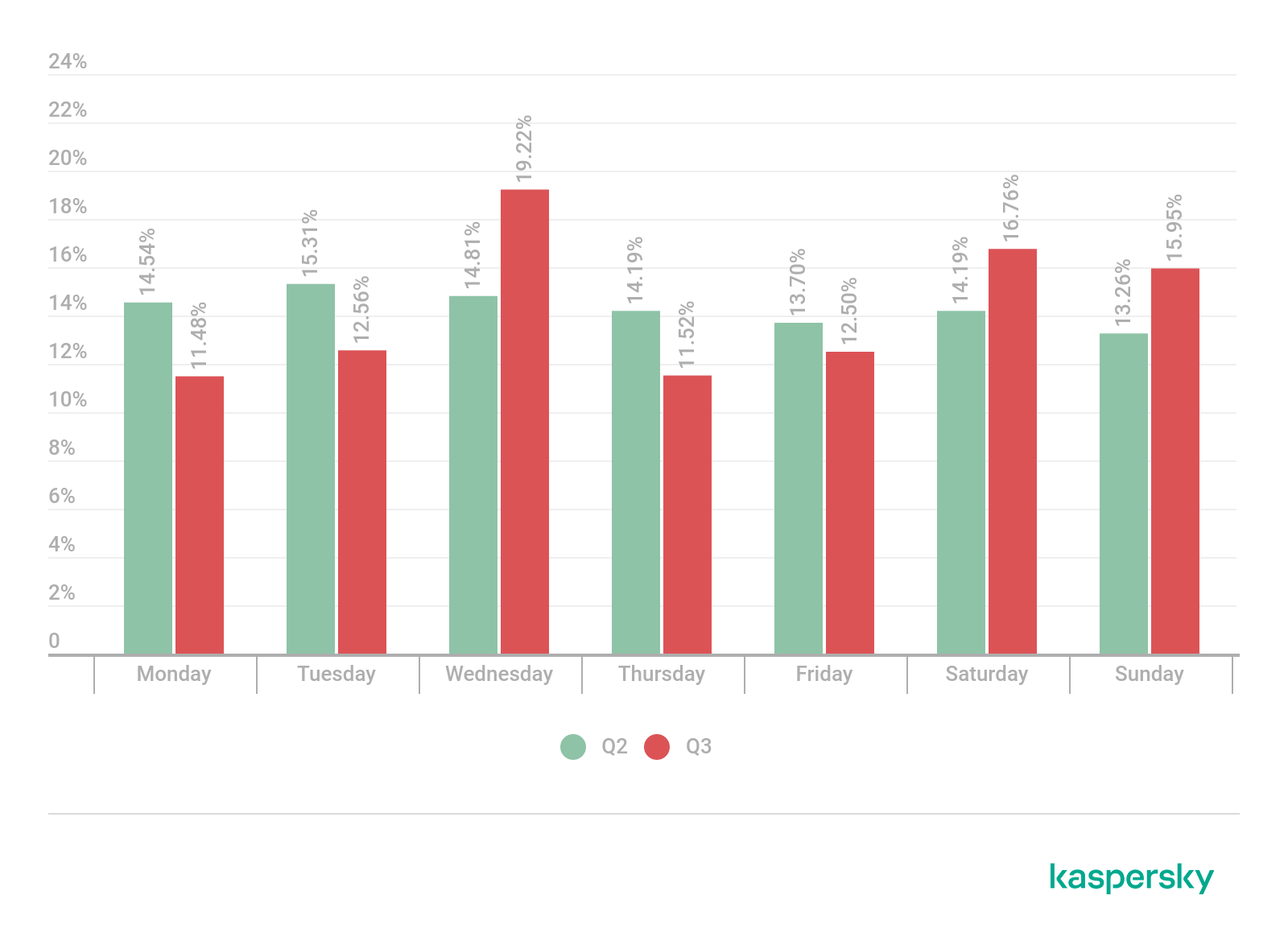
Distribution of DDoS attacks by day of the week, Q2 and Q3 2021 (download)
Duration and types of DDoS attacks
In Q3, the average DDoS attack duration reduced to 2.84 hours. This may be due to the decreasing number of attacks lasting 50 hours or more and a rise in relatively short attacks. For instance, even though the share of very short attacks (86.47%) dropped from the previous quarter, their number almost doubled: 63.7 thousand versus 33 thousand in Q2. Meanwhile, the longest attack of Q3 lasted for 339 hours — over 2 times less than the longest one of the previous reporting period.

Distribution of DDoS attacks by duration, Q2 and Q3 2021 (download)
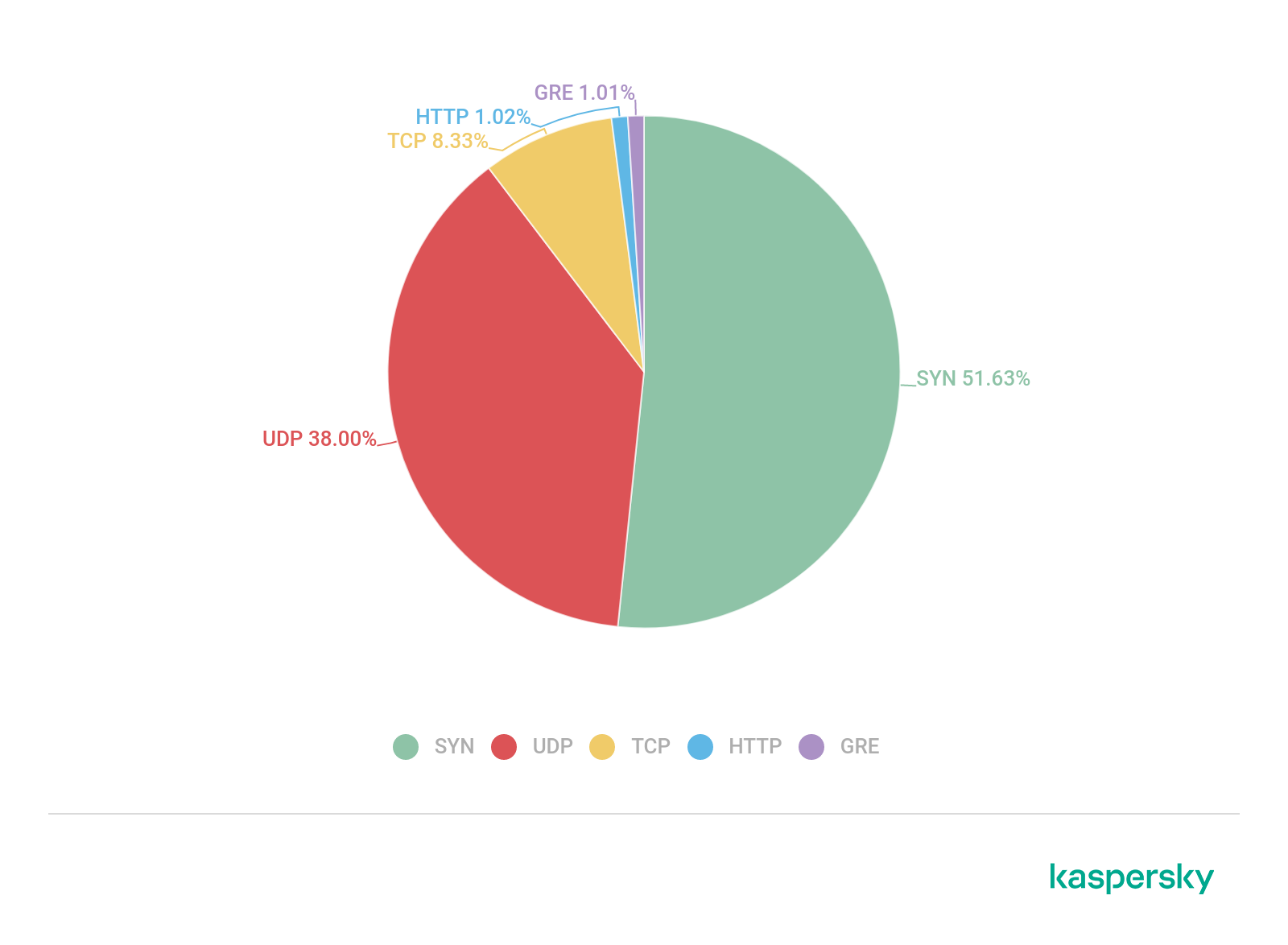
Distribution of DDoS attacks by type, Q3 2021 (download)
Geographic distribution of botnets
In Q3, most of C&C botnet servers were located in the US (43.44%); however, their share was down by 4.51 p.p. Germany (10.75%) remains second, its share also slightly reduced, with the Netherlands in third (9.25%). Russia (5.38%) has made it to the fourth position replacing France (3.87%), which is now sharing the sixth and seventh places with the Czech Republic (3.87%), and Canada remains in fifth (4.73%). The UK (2.58%) is eighth by the number of C&C servers, with Romania (1,94%) and Switzerland (1,94%) rounding out the ranking.
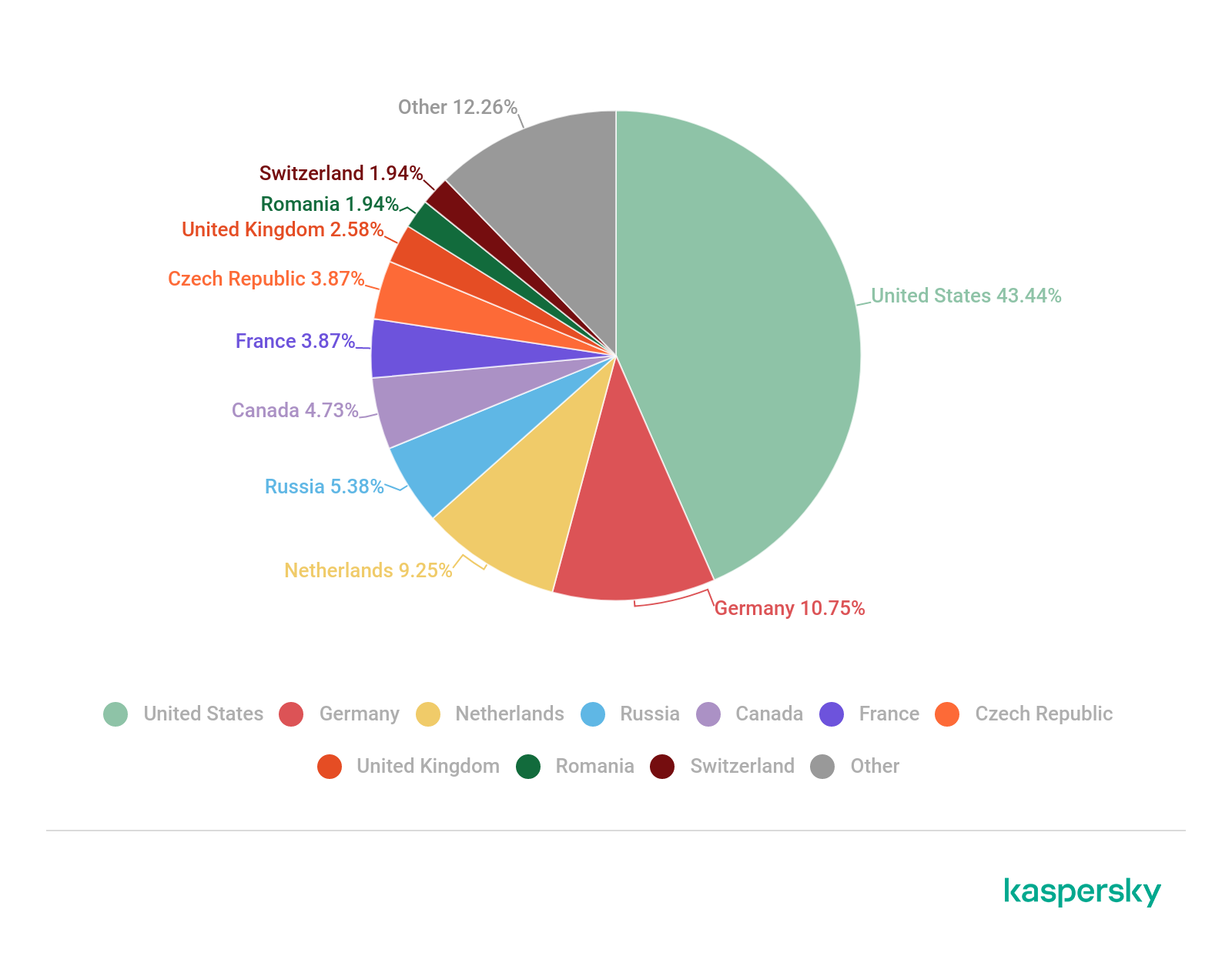
Distribution of C&C botnet servers by country/region, Q3 2021 (download)
Attacks on IoT honeypots
Same as last quarter, most of the active bots that attacked Kaspersky SSH honeypots to add them to their botnets were operating from China (30.69%), the US (12.59%) and Germany (5.58%). Brazil (5.53%) came in fourth, with India (4.09%) fifth and Vietnam (3.48%) sixth. Russia (2.67%) is seventh by the number of bots, and the source of 34.39% of attacks on SSH traps. Quite a few attacks came out of Ireland (23.36%) and Panama (19.58%) — the countries we already heard about in Q2. Ireland was home to 0.21% of attacking devices, Panama to 0.09%. Notably, it takes just one powerful bot to launch multiple attacks on IoT devices.

Geographic distribution of devices from which attempts were made to attack Kaspersky SSH honeypots, Q3 2021 (download)

Geographic distribution of devices from which attempts were made to attack Kaspersky Telnet honeypots, Q3 2021 (download)
Conclusion
Q3 proved unexpectedly fast-paced for DDoS attacks: our records show several thousand attacks per day on some days. Yet the duration of attacks — both average and maximum — reduced from Q2, meaning that we saw very many shorter attacks during the period.
Q4 is traditionally eventful in terms of DDoS attacks: companies that were on summer vacation get back to work, massive holidays and sales stimulating the battle for the buyer — even waged using less than legal methods. There is no reason to hope this year’s fourth quarter will be any different. Even though bitcoin has again reached its all-time maximum this October — likely to trigger yet another redistribution of capacity towards mining —we expect the number of attacks to grow and would be quite surprised to see it hover at the same level as in Q3 or lower
DDoS attacks in Q3 2021


















Brian
where is the total number of attacks? Or even average number of attacks per day? It’s nice to know what the min/max were, but they are outliers at the end of the day.
Securelist
Hi Brian!
The total number of attacks for Q3 is 114 006; on average we observed 1494 attacks per day.
All daily numbers are on the graph in this section (it is interactive): https://securelist.com/ddos-attacks-in-q3-2021/104796/#dynamics-of-the-number-of-ddos-attacks
Amy walker
What about google? I see does attack on my home network all the time and the IP address is google and Facebook. I’d like to know more about that.
Securelist
Hi Amy!
If we observe misuse of any services in DDoS or other attacks, we’ll mention it in our future reports. To solve issues with your home network, please contact your internet provider’s tech support.
If you want to know more about how to optimize your home Wi-Fi, you can find some tips here: https://www.kaspersky.com/blog/make-home-wifi-great-again/35043/